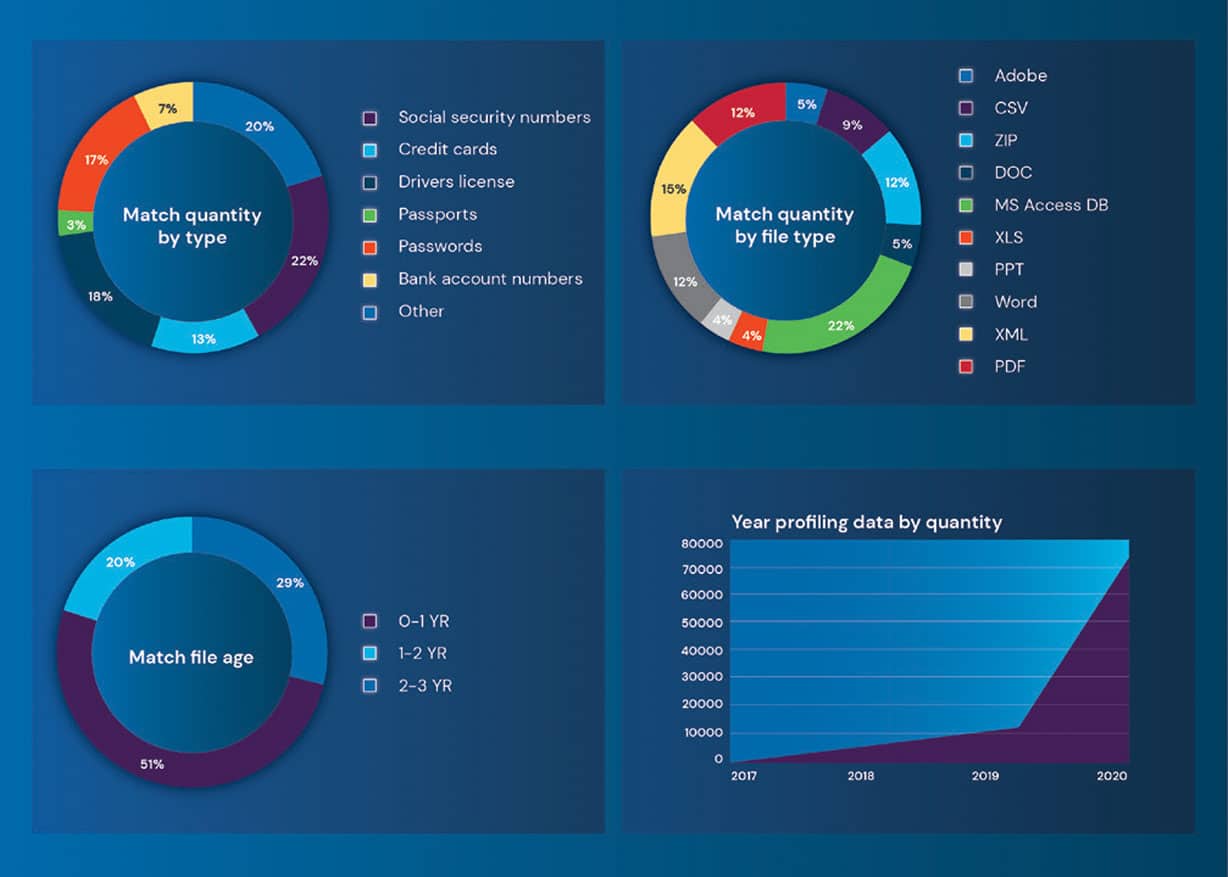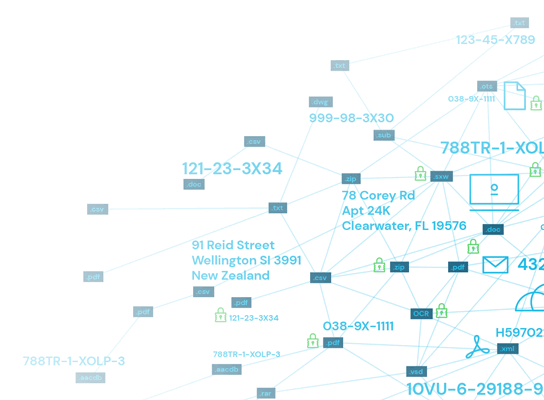
What is a Data Risk Assessment (DRA)?
Many organizations understand the importance of protecting personally identifiable information, but not all know how to properly perform a data risk assessment. Here’s what you need to know to secure data in your organization.
Organizations that store personally identifiable information (PII) present an attractive target to criminals. Unfortunately, many companies storing sensitive data are not properly tracking sensitive data and where it lives, resulting in exploitable vulnerabilities that can lead to costly data breaches.
As a protective measure, organizations should regularly perform data risk assessments to review and protect sensitive information. But what is a data risk assessment and what’s the best way to perform one?
What Is a Data Risk Assessment?
A data risk assessment is the process by which an organization reviews sensitive data under its control. This includes all data stored, accessed, and managed across the organization’s IT ecosystem, including all platforms, server locations, and cloud environments.
What constitutes sensitive data?
Before your organization can properly protect its sensitive data, you must first understand the data contained on your systems. This is why proper data classification is essential for data security.
When determining the data that should be classified as sensitive, keep in mind:
- The types of data used across the organization
- Locations where data may rest
- The overall value of the data to the organization
- Regulatory compliance requirements for your industry
- Access authorization rights
Unfortunately, many organizations rely on manual classification, which can quickly be outdated should classification guidelines change without proper updates to affected information. Worse still, much of 90% of organizational data is dark data, which is data that has either been captured and lies unused or data that companies are unaware they have in their possession.
How Can a DRA Help Protect Your Organization
A data risk assessment can shed light on the sensitive information your organization has in its possession. Additionally, this increased visibility can provide better insight into potential risks the organization may face, both malicious and accidental.
Several key outcomes of an effective data security risk assessment plan include:
- Decreasing the footprint of sensitive information. This allows data security plans in place to work more efficiently.
- Addressing authorization oversights. A data risk assessment can highlight users with either too much or too little access to sensitive information. In the former case, access can be reduced to decrease risk of improper access, while addressing the latter can improve organizational efficiency.
- Enacting proper security measures. An effective risk assessment allows an organization to address security shortcomings by putting a data protection program into place or shoring up existing vulnerabilities.
- Reducing operating costs. With a better understanding of the data under their control, an organization can focus resources on critical data and infrastructure. A proper plan can also mitigate costs in the event of a data breach.
Components Of a Data Risk Assessment
A data risk assessment can be broken down into three distinct pieces: discovery, assessment, and action. In many cases, each of these steps are performed concurrently, particularly in scenarios dealing with sensitive data.
Additionally, risk assessments should be performed regularly. Though various recommendations exist for how often assessments should take place, the nature of the business, the data being managed, and the outcomes of previous assessments will determine how often your business should conduct security assessments. It should be noted, however, that risk is never static in any case, and the nature and frequency of assessments should be an ongoing conversation within your organization.
Discover and classify organizational data
Without proper data discovery and classification practices, your risk assessment will be suboptimal. You must know where all of your data lives as well as its sensitivity level to ensure data is classified in accordance with an internally established framework. Keep in mind any regulatory requirements you may encounter, as well.
When determining classification levels, consider the following variables:
- Confidentiality. Who should be accessing the data?
- Value. How important is the data to organizational operations, and what harm could befall the organization if the data is accessed by an unauthorized party, modified, or destroyed?
- Usability. How readily available must the data be in order to conduct day-to-day business operations, and will overly restrictive protocols hinder operations?
While some organizations choose to tackle these classification tasks manually, this chore is often not sustainable or scalable, particularly in highly regulated environments. By requiring user input and enforcement, classification is slow, inefficient, and unable to adapt to changing organizational needs. For this reason, it is best to consider an automated approach to classification to ensure the best possible outcomes.
Assess Data Security Risks
Security risks can take many different forms. While direct attacks like ransomware, phishing attacks, or similar events are an obvious and growing threat, these are not the only entry points for data breaches. Not all risks can be attributed to malicious intent, either. Often, accidental oversight can be just as dangerous.
Common risks to data include:
- Poor password management. More than 60% of breaches can be traced back to easily determinable or otherwise weak passwords.
- Third-party access. If outside parties given access fail to enact proper data security measures, your systems can also be compromised.
- Unintentional access. Without proper credentialing, employees or other individuals within your organization can access sensitive information either intentionally or accidentally.
- Misplaced and stolen endpoint devices. Data kept on laptops, hard drives, or other unencrypted devices can easily fall into the wrong hands.
While this list is not exhaustive, it represents a sampling of the threats your organization may face. To determine the unique risks within your organization, you will need to include the viewpoints of your entire leadership team, not just your IT department. By bringing in additional perspectives, your organization will be better prepared to deal with threats.
Take Action To Mitigate Risk & Prevent Threats
Finding your data where it lives and identifying threats is all for naught if your organization fails to address the risks uncovered during the assessment. Threats to your data must be addressed as soon as possible to reduce the likelihood of data breaches and other security risks. From basic endpoint security to full policy changes at the company level, here are some of the ways in which your organization may need to address risks:
- Implement safeguards like backups and data encryption to better protect data.
- Create a company culture that recognizes the importance of data security.
- Build a comprehensive data breach response plan to mitigate damages and improve response
- Address data security needs with powerful security and privacy products.
How To Proactively Address Data Security Needs
The best way to prepare for a data security risk assessment is to protect sensitive data with a customized solution for your organization.
A tool like the Spirion Governance Suite allows your organization to take a forward-thinking approach to data security through automated, real-time, and persistent data classification. This strong base creates the ideal conditions in which to begin your data security risk assessment.
Further, the Governance Suite monitors data and identifies threats to determine if sensitive data is ever at risk, and can offer remediation strategies to address vulnerabilities within your organization. The software can also efficiently fulfill data subject access requests (DSAR) to ensure compliance with applicable regulations.
See how Spirion Data Risk Assessments gets your data out of the dark.
Use Spirion to get a snapshot of your threat surface with accuracy that can be depended on.