Data inventories are directories for managing sensitive data throughout an enterprise. Organizations can leverage those inventories to achieve and maintain compliance with the CCPA, GDPR, and other similar data protection laws and regulations.
There are a few primary ways any business can leverage their data inventories:
- Fulfill individual rights requests
- Conduct risk assessments
- Manage personal data sharing and permissions
- Develop breach notification
- Manage data protection programs
Use the links above to learn about specific sensitive data management approaches, or continue reading to read more information about data inventories and CCPA and GDPR first.
The relationship between data inventories and personal data
Before we dive into how organizations can leverage data inventories for compliance, it’s important to review the relationship between data inventories and personal data. Data inventories are living directories or systems for managing sensitive data across the enterprise. Sensitive data isn’t necessarily just personal data—it also includes trade secrets, attorney-client privileged information and export-controlled data.
Data inventories are the core of any data protection program. They provide leaders with a “single source of truth” for making decisions, while enabling them greater control and command over their programs. A poorly managed or underutilized data inventory can easily leave a data protection leader feeling overwhelmed on how to approach the litany of compliance mandates and regulations they need to keep up with. The good news is that any organization can leverage their data inventory to make CCPA and GDPR compliance easier.
What is personal data?
To ensure CCPA and GDPR compliance, your team needs to understand how the laws define protected personal data.
According to both the CCPA and GDPR, personal data is any information that identifies, relates to, describes, is capable of being associated with, or could be reasonably linked to to a particular person.
However, there are a few noteworthy differences between how the CCPA and GDPR view personal data. Let’s take a look.
Personal data under the CCPA
This act features many categories of personal information, including:
- Regular and machine-readable data
- Education, employment, employment history
- Protected classifications (e.g., Title VII)
- Commercial records of consumer purchases
- Biometric information
- Internet search and browsing; interaction with online advertisements
- Geolocation information
- Audio, electronic, visual, thermal, olfactory, or similar information
- Professional or employment-related information
- Education information as defined under federal law
- Inferences drawn from any of the above
Due to the broad nature of these categories and the CCPA’s definition, many things can be considered personal data. This applies to seemingly innocuous information like GPS coordinates that, if compiled, can infer a surprising amount of data about someone.
Personal data under the GDPR
Personal data under the GDPR falls into one of roughly three categories:
- Regular personal data: Social security, drivers’ license, and phone numbers; street addresses; dates of birth
- Machine-readable data: IP and MAC addresses, IMEI/IMSI/ESN, geo-location/GPS, log files, cookies
- Special personal data: EU special data (healthcare, political/religious, trade union, sexual, etc.)
While the CCPA has been described as “California’s version of the GDPR,” the CCPA clearly has its own nuances to be aware of. Even so, there are numerous compliance areas that are common to both laws and in these instances, data inventories will act as a “feeder” that advances compliance by providing crucial information.
How to fulfill individual rights requests with data inventories
Data subject rights under GDPR and consumer rights under CCPA center on the generally accepted privacy principles (GAPP) of notice, choice and consent, and access.
Chapter III of the GDPR, for example, encompasses well-known rights such as transparency of privacy practices, access to personal data, and the right to erasure (popularly known as the “Right to be Forgotten”).
Sections 110(b) and 105(c) of the CCPA mandate the disclosure of personal information and deletion upon request.
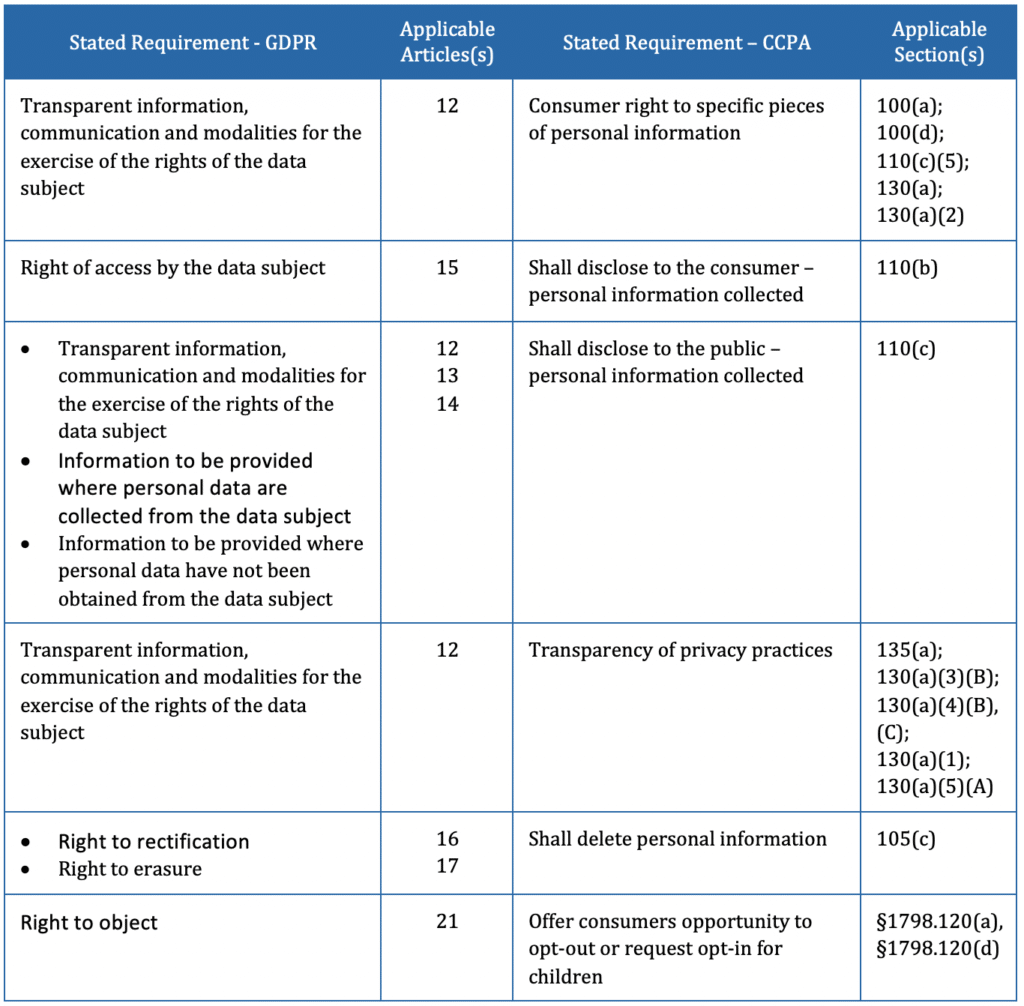
Data inventories advance the fulfillment of these requirements by identifying the following information.
What personal data is being collected in the course of business
A good first step is mapping out and reviewing processes with your internal teams but the truth is, many times pieces of personal data may be accidentally collected or go unseen. A good data discovery tool with the ability to search for both structured and unstructured data can help your organization get a clear, thorough view on what types of personal data is being collected.
Specific information collected about a particular individual
Organized, well-managed data inventories can make it easier to search for an individual and zoom in on all the information associated with them. When data inventories are managed manually, you can never completely rule out the possibility of human error. This is where a data platform with AI-driven name recognition and identity matches can help you connect sensitive data with the correct, verified identity. This automated process streamlines the fulfillment of individual rights requests, while eliminating human error.
Where personal data is located across the enterprise
To ensure an up-to-date data inventory, data discovery tools that can search for all types of data, regardless of where it lives, is critical. This means it should have the capability to search across your entire enterprise, from on-premise systems to the cloud. It’s not uncommon for organizations to find complete, hidden troves of data after discovery is performed.
Using data inventories to conduct risk assessments
Risk assessments are processes for identifying threats and vulnerabilities and prioritizing their resolution. When developed correctly, risk assessments ensure that data protection expenditures reap the best value in terms of budget and time.
All or nearly all modern data protection laws mandate a risk assessment in some form. Sometimes the phrase “risk assessment” is explicitly cited (i.e. NYCRR Part 500). But more often, it’s not quite as succinct. Article 32 of the GDPR is one example, featuring a risk “preamble”, a mandate for the implementation of controls, and then a list of examples of such measures.
The CCPA is a little more straightforward, mandating that businesses “implement and maintain reasonable security procedures and practices appropriate to the nature of the information.”
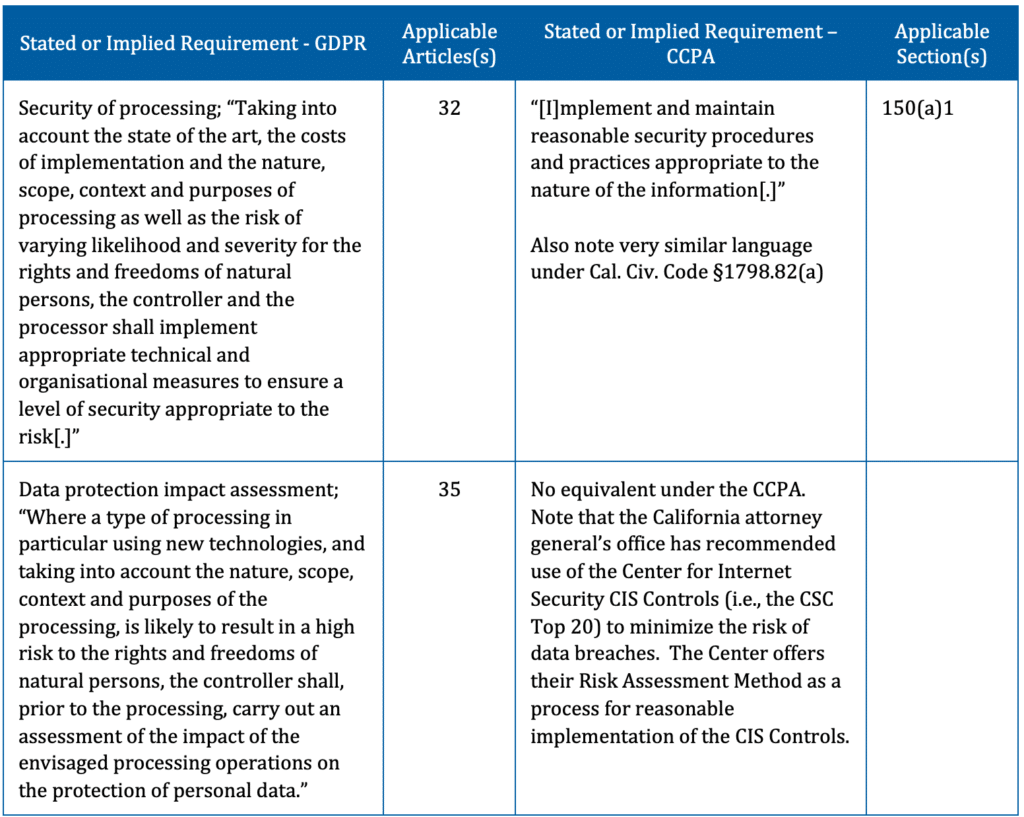
Under either of these approaches for the CCPA or GDPR, data inventories serve as a feeder. They “feed”, or provide, details on:
- The individual data elements processed
- Which applications share and process the data
- Who data is shared with, both internally and externally
These details are essential to creating risk assessments that meet the requirements enforced by the CCPA and GDPR. Automated data discovery can help create a more accurate data inventory filled with these details while simultaneously cutting down on hours of manual work and human error.
How to manage sharing of personal information with data inventories
Sharing of personal data can present many challenges to an organization. This is because the responsibilities for protecting that data are multiplied among recipients.
Take for example, this case that involves the licensing of personal data to Cambridge Analytica by Facebook. In this scenario, Facebook missed several opportunities to prevent misuse of that data, which resulted in a $5 billion fine against the company. The idea of policing the sharing of personal data was popularized by the EU Data Protection Directive 95/46/EC. There, sharing of data was referred to as an “onward transfer.”
The GDPR uses this same language and devotes Chapter V (Arts. 44 – 50) for the associated requirements. The CCPA takes the limiting of onward transfers a step further. It offers California consumers the ability to tell businesses not to transfer personal information and their third-party recipients not to use it.
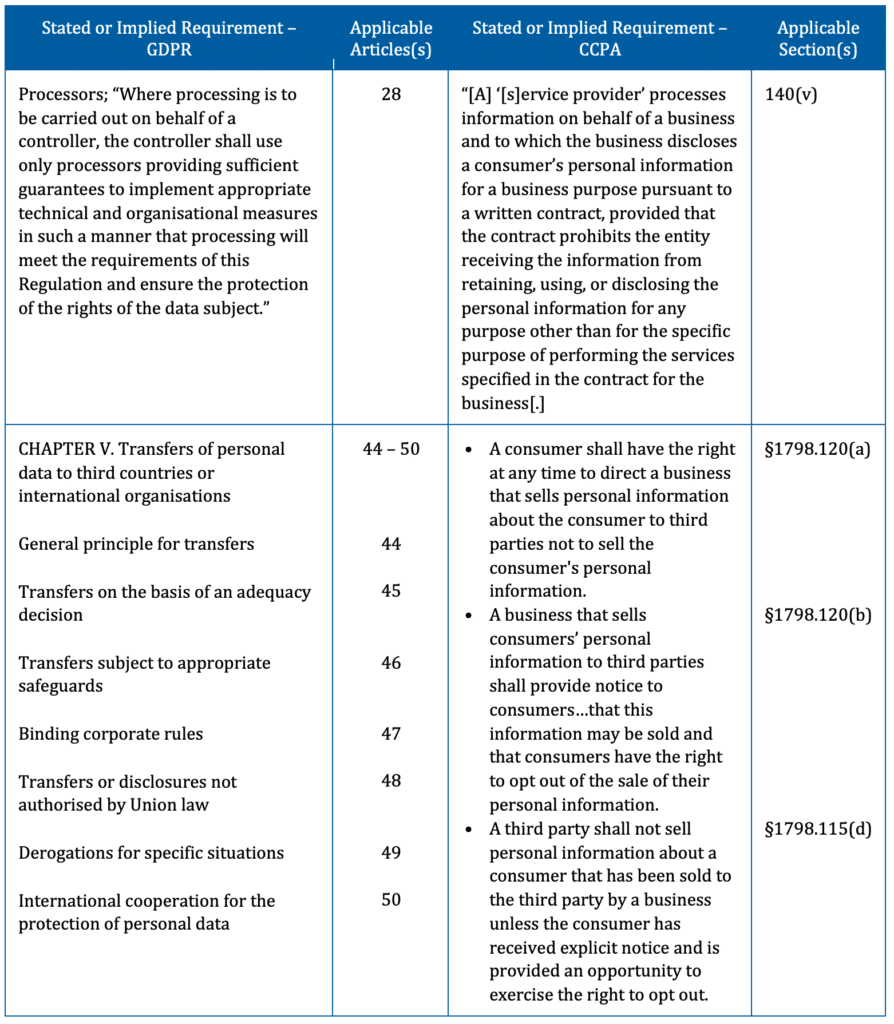
Data inventories advance data sharing compliance by:
- Identifying third-party recipients of personal data, as well as what is being transferred
- Helping distinguish between users or entities that are merely processing or providing some service, from those that are using it for their own purposes
How to develop breach notification plans using data inventories
Breach notification is the process of determining the scope of a sensitive data breach, evaluating its severity, and notifying regulatory authorities and likely victims. It is a distinct process from incident response, which is mostly centered on “battling the bad guys” and re-establishing the integrity of the organization’s infrastructure.
One of the most important aspects of breach notification is rapidly assessing the details of the breach and providing actionable information to authorities and victims. Under the GDPR, the organization (or data controller) suffering the breach must notify authorities “without undue delay and, where feasible, not later than 72 hours after having become aware of” the breach. It must also notify victims without undue delay when there is a high risk to their ‘rights and freedoms’.”
While the CCPA is not, per se, a breach notification statute, California Civil Code §1798.82 requires victim notification “in the most expedient time possible and without unreasonable delay.” That law cites specific information that must be included in a notice, which is also true of the GDPR.
Data inventories advance the fulfilling of these requirements by helping organizations identify:
- The types personal data in its possession and the individual elements
- The personal data implicated or likely implicated in the breach
- The business and technical owners of the underlying application program or process that uses the personal data
How data inventories help data protection officers manage protection programs
When it comes to breach notifications, many organizations may choose to appoint a data protection officer (DPO). Appointing a DPO is mandated when the processing taking place “require[s] regular and systematic monitoring of data subjects on a large scale” or involves “special personal data” (healthcare, political or religious beliefs, etc.) on a large scale.
While the CCPA does not specifically mandate the appointment of a DPO, the complexity and scope of the law necessitates that someone with intimate knowledge of their organization’s collection and processing of personal information be appointed to lead the program. The same is true for those EU-based organizations that aren’t required to appoint a DPO.
To this end, DPOs and data protection managers can leverage data inventories to:
- Identify data subjects, consumers and data elements being processed
- Gain insight into how much an organization knows about an individual
- Minimize the volume of personal information it has in its possession and associated risks
A complete sensitive data platform that has visibility into data wherever it lives, offers automated workflows for discovery, classification and remediation, and quickly matches verified identities with their associated data, makes a DPOs job much easier. With the ability to rapidly connect and understand all the data on hand, your team’s DPO can focus on making strategic decisions rather than be bogged down by tedious tasks.
Data inventories: the cornerstone of CCPA and GDPR compliance
Data inventories are a necessary and valuable directory of an organization’s sensitive data. The purpose of an inventory is to serve as a “single source of truth” for data protection team leaders and enable them to quickly and accurately answer questions like:
- What sensitive data are we collecting and using?
- Where is it located throughout our organization?
- Who has access to it?
- With whom is it being shared?
- How is it protected and who is responsible for it?
Remember these 5 ways to advance your organization’s compliance
In summary, there are at least five ways to advance compliance under the CCPA and GDPR by leveraging data inventories:
- Meeting the requirements of data subject rights, such as the right to deletion.
- Conducting risk assessments, including Data Protection Impact Assessments (DPIA), in order to determine appropriate controls.
- Determining which third parties have access to personal data and in what capacity.
- Developing breach notification plans and providing actionable information to affected parties in the event of a breach.
- Assisting Data Protection Officers (DPO) and other staff in executing their day-to-day duties.
With today’s privacy law landscape, there’s a constant need for timely, accurate information about an organization’s sensitive data and how that data is being used, shared, and protected. As such, data inventories represent the cornerstone of compliance with the CCPA, GDPR and other equally demanding data protection laws.
Watch this free demo to see how Spirion can help you meet your compliance obligations with data protection.


