
BY RYAN TULLY
September 30, 2024
Not all data is created equally — which is why it’s integral for organizations’ security teams to proactively identify, assess and classify sensitive data. Even if a piece of data is categorized as “sensitive,” the legal, reputational and financial consequences of a breach may not always look the same between two pieces of sensitive data. There are varying degrees of data sensitivity.
For example, unauthorized access to a person’s employment contract will probably not result in the same ramifications as unauthorized access to a person’s social security number. While both pieces of data are considered sensitive data that must be protected, the aftermath of a breach or leak looks very different.
One of the foundations to determining the sensitivity level of data is to think about how the loss of the confidentiality, integrity, or availability of that information would impact your organization in the case of an unauthorized disclosure. Here, we walk you through the types of sensitive data you need to be aware of, important security objectives to consider when assessing data, and what to do once you’ve determined the data’s level of sensitivity.
What is sensitive data?
Before we dive in, let’s address what sensitive data is and how it differs from personal data. Sensitive data is classified information that must be protected against unauthorized access, and it can be seen as a higher tier that requires greater protection than personal data.
Many things can be considered personal data, such as an individual’s name or email address. Sensitive data, on the other hand, will generally be information that falls under these special categories:
- Data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs
- Data that reveals trade-union membership
- Genetic and biometric data used to identify an individual
- Medical and health-related data
- Data pertaining to a person’s sex life or sexual orientation
Types of sensitive data to look out for
Sensitive data can be a number of things. One of the easiest ways to evaluate is to think of personal data you would not want to be openly shared with just anyone. There are, of course, federal laws and regulations that set specific guidelines on what types of sensitive data must be protected, like:
- Financial information – Credit card numbers, bank account information, and social security numbers.
- Government information – Any document that is classified as secret or top-secret, restricted, or can be considered a breach of confidentiality.
- Business information – Accounting data, trade secrets, financial statements or accounts, and any sensitive information in business plans.
- Personal information – Addresses, medical history, driver’s license numbers, or phone numbers.
This data is information most people would not want shared with others who don’t have approval, and it’s the responsibility of the organization that has collected that data to protect it from unauthorized access.
Potential risks of sensitive data loss
Unauthorized access or loss of sensitive data can pose major risks for companies. Most of these risks stem from three challenges for organizations:
- How to identify sensitive data and locate it. The first obstacle that organizations must overcome is how to identify their data at hand and how to locate it within the company database. Think of how data travels throughout your organization—there are likely hundreds of repositories and it’s nearly impossible to identify and keep tabs on all of them manually. Not only would it be difficult for your IT and security teams, but it would also be a waste of time. Instead, organizations can implement AI-powered sensitive data discovery tools that automate the process and achieve greater accuracy than the human eye.
- Understanding data compliance and privacy laws. Once sensitive data has been found, your team needs to understand how your organization plans to use it and protect it in accordance with data privacy laws, like the GDPR, CCPA and HIPAA.
- The ability to monitor data in real-time. Data moves quickly, so your team should also have the ability to observe and assess risks just as fast. To do this and be proactive with trends in how sensitive data is being used against consumers, you need to be able to monitor your organization’s entire data landscape in real-time.
If your team can do these three things, you’re on the right path to safeguarding sensitive data. And, as you can see, data discovery and classification are the essential first steps that enterprise organizations can take to monitor sensitive data and minimize risks for the future.
Once this foundation is in place, you can reduce your sensitive data footprint, monitor how data moves and use automated workflows and notifications as best practices to keep your security program strong—all crucial to preventing a data breach from occurring.
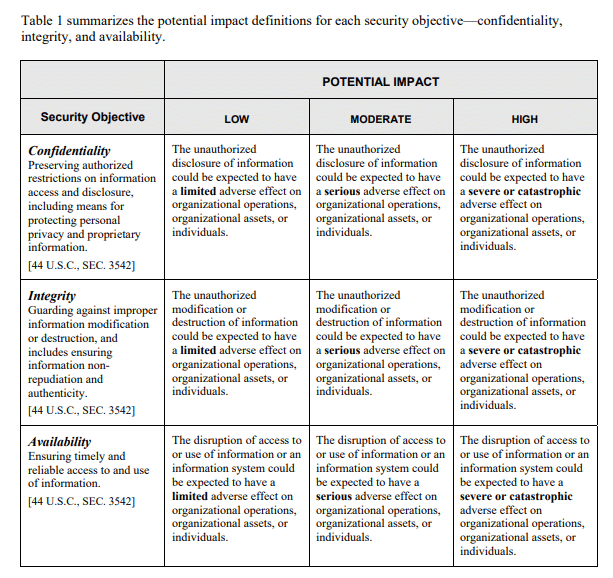
Security objectives to help determine level of data sensitivity
The first step to creating any plan is determining goals and objectives. Regardless of the company or organization, most security teams share common goals when it comes to data security. Below, we’ve outlined the top three most common security objectives and how each can be used to determine the possible impact level of a potential data breach.
- Confidentiality: Preserve authorized restrictions on information access and disclosure, which includes protecting personal privacy and proprietary information.
- Integrity: Guard against improper information modification or destruction, which includes ensuring informations’ non‐repudiation and authenticity.
- Availability: Ensure timely and reliable access to and use of information.
A violation of any of these objectives can result in limited (low), serious (moderate) or severe (high) adverse effects on an organization’s operations, assets or individuals. As the potential impact level moves from low to high, the classification of that data’s sensitivity level should increase respectively.
The following table from the Federal Information Processing Standards (FIPS) publication 199, published by the National Institute of Standards and Technology (NIST), provides a framework for determining the impact that can be applied to the sensitivity of the information.
Creating a data classification policy to determine data sensitivity impact level
Data classification is a fundamental step to protecting proprietary information. Since various pieces of data have varying levels of sensitivity, there are different levels of protection and unique procedures for remediation. If you play a key role in your company’s data security, understanding of the level of sensitivity required for each piece of data is a crucial piece of the data security puzzle.
As a general rule, there should be a minimum of four data classification levels.
- Public – Which data is fine to share with the public? Anything that is not personal or sensitive, such as a person’s name. This means that there would be little to no risk if this data were accessed. This type of information likely does not need to be encrypted or have major protection.
- Internal – This is data that is not meant for public disclosure but also has low security requirements. Some examples of internal data are a company’s sales playbook or organizational chart. While an organization wouldn’t want this data to leak and may suffer some short-term reputational embarrassment, unauthorized disclosure of this information wouldn’t result in severe non-compliance repercussions.
- Confidential – Access to this data would cause a moderate risk to the person or organization affected. The consequences are greater than short-term embarrassment and could have a negative impact on company operations or long-standing reputation.
- Restricted – This is the highest level of sensitive data that if compromised, could put an organization at great financial, legal, regulatory and reputational risk. Some examples of this include customers’ Personally Identifiable Information (PII), Protected Health Information (PHI) and credit card numbers.
Many data security policies have been created and adapted across the business world to help protect organizations and consumers. Various companies and agencies have in-house security policies as well. There are several industries that must take extra precaution when identifying and classifying sensitive data, either because of the volume of sensitive data processed or industry-specific laws and regulations they must adhere to. For instance, healthcare organizations have specific legal acts and policies they must comply with, like HIPAA.
Benefits of sensitive data discovery and classification
When it comes to locating sensitive data, determining its level of sensitivity, and protecting that classified information, sensitive data discovery and data classification are at the core of everything you do. Here are the benefits your organization will see after implementing these practices.
Sensitive data discovery benefits
- Know your data’s location, volume, context and more, no matter where it lives in your organization’s systems.
- Discover data that’s hard to find and usually remains hidden, like unstructured data.
- Reduce your team’s sensitive data footprint to only what’s necessary to operate to decrease risk.
- Utilize your security budget more efficiently by implementing strong security measures only on the data that requires it.
Data classification benefits
- Take ownership and control of your data.
- Make business practices and workflows more efficient, since you can easily search for data by classification type and always know what type of data you have on hand.
- Comply with rules, regulations and privacy laws to protect your customers and your organization’s reputation and financial standing.
- Spread awareness company-wide of how data should be handled per data protection policies and procedures.
Safeguard sensitive data with a leading-edge sensitive data platform
When it comes to managing your company’s data lifecycle and adhering to compliance laws and regulations, determining the level of sensitivity and classifying data is an integral step in the process. At Spirion, we are here to help protect and secure business’ and consumer’s sensitive data with data classification tools.
